Security often gets pushed to the end of electronics development. Teams focus on the nuts and bolts of things like PCB assembly. They design with an eye to functionality first and plan to add security features later. But by the time your product is built, vulnerabilities are already in the design.
Adding security after the fact doesn’t work. Software patches alone cannot fix weak firmware, unsecured communication protocols, and unprotected components.
This guide will show you how to build cybersecurity into electronics from the start. You’ll learn which components include security features, how to protect firmware and data transmission, and what to look for in manufacturing partners. By the end, you’ll know how to create devices that resist attacks by design.

(Kerfin7/Freepik)
The Threat Landscape for Modern Electronics
Electronic devices have multiple vulnerabilities that make them susceptible to cyber attacks. Hackers can exploit these devices via weak firmware, unsecured wireless protocols, or poorly protected communication channels. Some devices even have compromised components from the supply chain, which introduces threats before the product ever reaches customers.
Different devices attract different types of attacks. Smart home devices get targeted for data collection and network access. Medical devices face threats from hackers seeking to manipulate device functions or access patient data. Industrial systems attract attackers looking to disrupt operations or steal proprietary information.
How to Protect Your Devices Against Cyber Threats
Cyber threats will continue to evolve as attackers find new ways to exploit electronic devices. Fortunately, there are steps you can take to minimize the risk of vulnerabilities in your products.
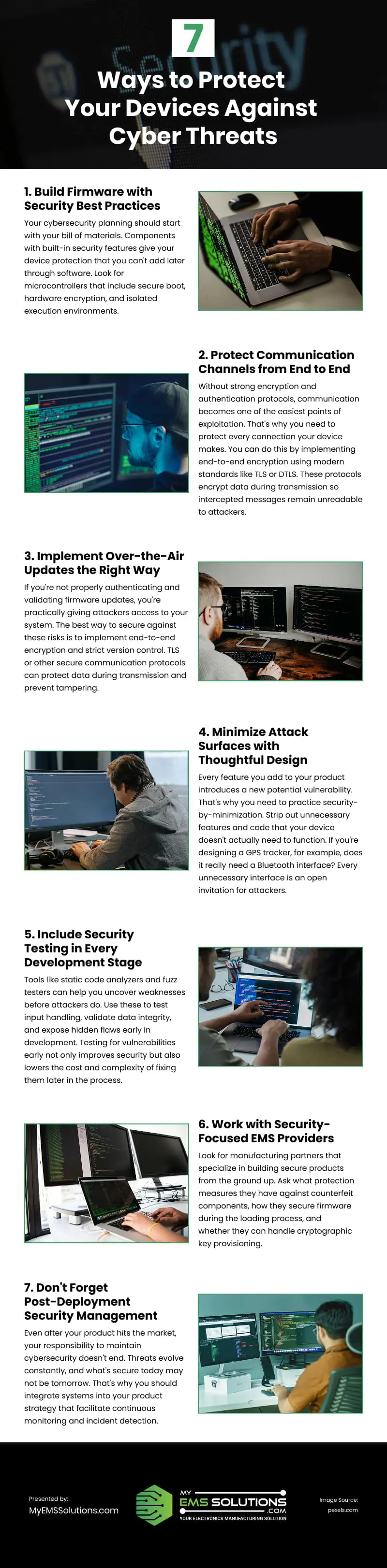
Build Firmware with Security Best Practices
Your cybersecurity planning should start with your bill of materials. Components with built-in security features give your device protection that you can’t add later through software. Look for microcontrollers that include secure boot, hardware encryption, and isolated execution environments.
These features work together to protect your device. Secure boot verifies that only authorized firmware runs on your device, blocking attackers from loading malicious code. Hardware encryption protects your cryptographic keys even if someone physically accesses the chip. Isolated execution environments keep sensitive operations separate from the rest of your system, so a breach in one area doesn’t compromise everything.
Protect Communication Channels from End to End
Your device might be physically secure, but what about the data it sends and receives? Without strong encryption and authentication protocols, communication becomes one of the easiest points of exploitation. That’s why you need to protect every connection your device makes.
You can do this by implementing end-to-end encryption using modern standards like TLS or DTLS. These protocols encrypt data during transmission so intercepted messages remain unreadable to attackers. If your device communicates wirelessly (via Bluetooth, Wi-Fi, or Zigbee), make sure to use strong passwords, rotating keys, and mutual authentication. Don’t assume that because your device is small or specialized, attackers won’t target it. That’s often what makes it attractive.
Implement Over-the-Air Updates the Right Way
Over-the-air (OTA) updates play a key role in fixing bugs and closing security gaps, but only when handled securely. If you’re not properly authenticating and validating firmware updates, you’re practically giving attackers access to your system. Each update should be cryptographically signed and verified by the device before installation.
The best way to secure against these risks is to implement end-to-end encryption and strict version control. TLS or other secure communication protocols can protect data during transmission and prevent tampering. For version control, ensure the device checks firmware version numbers before installation to block any downgrade or rollback attempts.
Minimize Attack Surfaces with Thoughtful Design
Every feature you add to your product introduces a new potential vulnerability. That’s why you need to practice security-by-minimization. Strip out unnecessary features and code that your device doesn’t actually need to function. If you’re designing a GPS tracker, for example, does it really need a Bluetooth interface? Every unnecessary interface is an open invitation for attackers.
You should also use hardware and software isolation techniques to separate critical systems from non-critical ones. For example, the part of your device that handles user input shouldn’t have direct access to memory areas where cryptographic keys are stored. Creating these boundaries helps limit the damage if one part of your system is compromised.
Include Security Testing in Every Development Stage
One of the most common mistakes in electronics development is treating security testing as a final checkpoint. In reality, you should integrate security assessments into every phase of your product lifecycle. From initial prototyping through production, make sure to test each iteration of your board and firmware for potential vulnerabilities.
Tools like static code analyzers and fuzz testers can help you uncover weaknesses before attackers do. Use these to test input handling, validate data integrity, and expose hidden flaws early in development. Testing for vulnerabilities early not only improves security but also lowers the cost and complexity of fixing them later in the process.
Work with Security-Focused EMS Providers
If you’re outsourcing your electronics manufacturing, don’t assume your partner will automatically prioritize security. A lot will depend on where and how they manufacture. For example, electronics manufacturing in the USA comes with stricter regulatory oversight and established security standards, so choosing a domestic partner gives you better protection for sensitive components and intellectual property.
Look for manufacturing partners that specialize in building secure products from the ground up. Ask what protection measures they have against counterfeit components, how they secure firmware during the loading process, and whether they can handle cryptographic key provisioning. Working with a security-focused manufacturer will help you maintain the protections you built into your design throughout the production process.
Don’t Forget Post-Deployment Security Management
Even after your product hits the market, your responsibility to maintain cybersecurity doesn’t end. Threats evolve constantly, and what’s secure today may not be tomorrow. That’s why you should integrate systems into your product strategy that facilitate continuous monitoring and incident detection
Consider deploying telemetry features that allow you to spot unusual behavior in the field, such as abnormal data transmission or unauthorized access attempts. If something suspicious happens, your system should be able to alert your team and, ideally, take automatic protective actions like shutting down certain features or isolating the device.
Final Thoughts
These are the steps you can take to protect your electronics from cyber threats. Remember that it’s always better to build in security during development than to patch problems after products ship.
Choose components with security features, write firmware that limits vulnerabilities, and encrypt your device communications. When you plan for security early, you avoid costly fixes and keep your products protected from the start.
Video

Infographic
In electronics design, security is most effective when incorporated from the outset. Focusing only on functionality can lead to overlooked vulnerabilities. Check out this infographic for tips on protecting your devices from cyber threats.